Penetration tests and security assessments are essential to understand your organization’s exposure to cybersecurity risks. However, they do not always prepare your employees, executives and Incident Responders against real threats. Red Team Operations aim to improve your asset’s and personnel’s readiness through a realistic security incident drill that can target your organization’s cyber, physical, and human information security elements.
Red Teaming is all about identifying gaps in
your security strategy
by thinking and working like the cyber criminal.
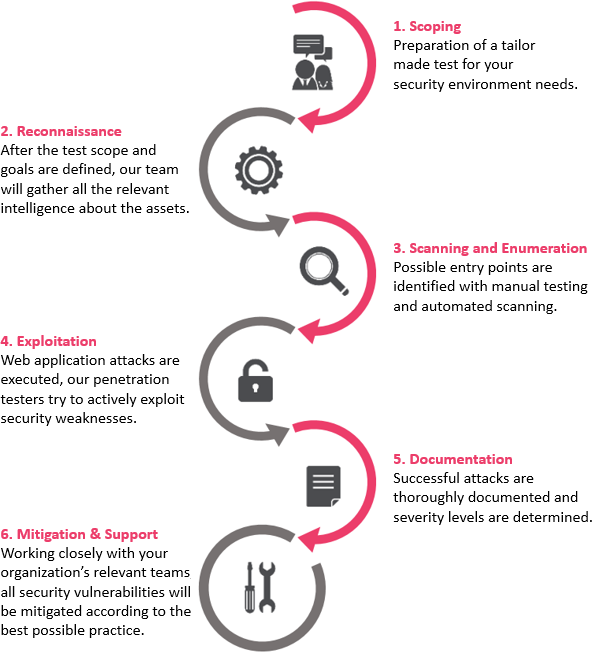
How do Red Team Operations work?
During red teaming engagements, Cyber Espial’s Red Team, composed of experienced cyber security specialists, designs realistic attack scenarios using gathered open source intelligence (OSINT) and threat intelligence relevant to your organization, and its IT infrastructure, personnel and premises.
Each attack scenario has a specific and tangible objective tailored to your organization (a.k.a critical functions or flags), which, under other circumstances, would cause significant damage to your organization’s assets, reputation or regulatory compliance. The objective may include the following:
- Unauthorized fund transfers
- Highly confidential data theft or exfiltration
- Access to highly sensitive physical locations
- Disruption of industrial processes or industrial control systems
The Red Team will then proceed with the defined scenario, by mimicking the tactics, techniques and procedures (TTPs) of real-life threat actors, putting your organization’s incident response and crisis management team (i.e. the blue team) to the test. For the operation to be effective, it is essential that the blue team members are not aware that the attack originates from a planned Red Team engagement. This will ensure they react as if a real security incident was underway.
At the end of the Red Team Operations, a debriefing is performed between the Red Team and the Blue Team (a.k.a replay session) in which an analysis of the executed scenario is made on both sides and key areas of improvement are discussed. In conjunction to this replay session, a Purple Team session can be conducted to deep dive on the lessons learned. As the simulated threat agent, the Red Team can propose additional steps that, when implemented, would improve the detective and preventive measures, and can highlight the actions the Blue Team could have taken to improve detection and response times.
The Benefits Of Red Teaming
The outcome of a red team assessment is evidence of flaws and security weaknesses that have been exploited within your organisation by the red team. These findings can be used to get buy-in from senior staff and to make security improvements across the organisation.
After a red teaming exercise, you will:
- Understand the impact of a security breach
- Discover weaknesses in your development and testing processes
- Collect evidence to justify security spending
- Identify vulnerabilities in applications and systems
- Measure the resilience of your organisation’s cyber defence
- Provide a practical training opportunity for SOCs
Post red teaming checklist:
- Action the recommendations from the red team
- Measure the results against KPIs Once implemented, repeat the
- process and improve it
- Then measure KPIs across all red teams to identify performance trends
- Refine your SOC capability until it can deal with an array of attack types and actors
- Remain vigilant!
Why choose Cyber Espial?
Choose our company for Red Team Assessments and unlock unparalleled cybersecurity advantages. Here’s why we stand out:
Elite Expertise: Our Red Team consists of skilled professionals with extensive experience in emulating real-world cyber threats, ensuring a thorough and authentic assessment.
Holistic Approach: We take a comprehensive view of your organization’s security, challenging all aspects of your defenses to identify vulnerabilities others might miss.
Tailored Scenarios: Our Red Team customizes attack scenarios to match your specific business environment, providing insights that align with your unique risks.
Strategic Insights: Beyond just discovering weaknesses, we provide actionable recommendations to bolster your overall security posture and incident response readiness.
Continuous Support: We engage with you throughout the process, addressing any concerns and providing clear communication from planning to post-assessment.
Regulatory Compliance: Our Red Team Assessments align with industry regulations, ensuring you meet compliance requirements and industry standards.
Real-Time Defense Strengthening: Gain an edge over adversaries by uncovering and mitigating threats proactively, elevating your cyber resilience.
Trusted Partnerships: We prioritize trust and confidentiality, building long-term relationships with our clients through transparency and proven results.

Protecting over 100 organizations of all sizes.
Only the best ethical hackers in the industry with vast experience in offensive and defensive security related activities.

Collaboration with Cyber Espial’s Research and IRT teams, positioning the CRT service as the most advanced cyber resilience test in the world.

Worldwide leader in securing SAAS, Global Banks and Retailers.
See Our Team In Action
Consult Our Team of Cybersecurity Expert For Your Business Penetration Test.
