CYBER ESPIAL (VRP)
Vulnerability Reporting Program
Cybersecurity experts in Asia are identifying vulnerabilities in your web-based applications. We streamline time-consuming tasks like report verification, POC verification, prioritisation of critical vulnerabilities, and triage, and recommend the best patch to assist your non-cyber team.

They Already Trust VRP!


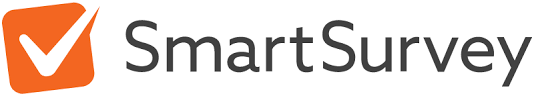


We Encourage
We invite community of cybersecurity researchers with diverse skillsets and specialities to find and report vulnerabilities in internet facing applications. We believe that researchers can find vulnerabilities scanners can't. We assist them on how to report their findings, so they get the appreciation and reward for their effort of securing the internet. Our team help them in polishing their skills by learning with real world attack surface.
We Assist
We assist companies by extracting fuzzy data, evaluating crucial from out-of-scope reported vulnerabilities and authenticating the POC so they patch and improve security posture within critical time period. We guide team to understand multiple attack scenario and focus on the asset types which are most prone to attack by documenting facts in the report.
What is a Vulnerability Reporting Program (VRP)?
A VRP is a program helps researchers to report security flaws in an organization’s internet-facing applications. Cyber Espial team receive, verify and triage vulnerabilities and submit reports with best understanding and solution for developers and security team to learn and secure attack surface like never before. VRP is a complete set of knowledge, expertise and skills which close the gap between vulnerability disclosure, verification, prioritization and remediation. The report gives insight into the most impactful weaknesses from a hacker perspective. VRPs improves security postures for mid-sized companies with zero security budget by sharing insight of attack vectors, focus to avoid risky misconfiguration and tracks remediation progress.

DISCOVERY
We assist cybersecurity researchers to probe your cyber defenses for vulnerabilities by following pro-active security approach. We guide them to report those vulnerabilities to our team via secure channel so we assess the risk and the attack surface and help them in receiving the recognition they rightfully deserve.
ASSESSMENT
Using a variety of factors, including previously reported vulnerabilities to SaaS vendors, exploit databases, bug bounty report's knowledge base, and communication with researchers to get the full picture, our team carefully evaluates the risk, severity level to your data, and business. Researchers must sign an NDA promising not to disclose the specifics of the vulnerability without first receiving your and your business's explicit consent.
ALERT
After thorough analysis, our VRP team notifies your team to vulnerabilities and the effects of potential attacks. Only the CEO, CTO, CIO, and security engineers receive emails from us. In response to the first email, team sends two additional emails. If we didn't receive any response from you, we'll not send further emails and will close the case.

SHARING
We share with you information about how researchers identify vulnerabilities, how we share reports, information about the researchers (if they permit us to share it with you), and how we define our fee structure. We might need to sign an NDA on your business' terms and conditions in order to guarantee data privacy, secure delivery, and deletion.
TRANSACTION
Researchers charge a fee for reports, which we handle on their behalf. The fee depends on a number of factors, such as the significance and severity of vulnerabilities, exploitation techniques, the bounty the researchers wish to avail, etc. You will be charged in two installments for the fee.

SUBMISSION
Our team will send you the vulnerability report via any of the secure channels and methods suggested. The report will detail the history of each vulnerability, proof-of-concept (POC) reproduction steps, severity, risk, and impact levels, method of exploitation, and patch. Our team triages and prioritises vulnerabilities in reports to ensure that critical issues receive immediate attention and knowing how attackers can exploit common vulnerabilities helps developers understand what, why and how to secure.

VALIDATION
We'll wait for you to confirm the report's veracity after it has been submitted. Our team has already verified POC. Until and unless your team verifies the validity of vulnerabilities we will not forward fees to cybersecurity researchers. If necessary, our team will join yours in verifying the vulnerabilities by imparting any research-related information that we collected.

PASS
If you accept the report, we will credit the fee to the security researchers. The remaining fee will then be collected by our team. As soon as developers apply the patch to the vulnerabilities, we'll analyse and confirm it again. Our team will be available around-the-clock to help if they need any assistance with the patching process.
REJECT
If you disagree with the report, we will request a valid legitimate response. If needed, we'll invite you and researchers in a meeting to determine whether the reported vulnerabilities were already known. The advance fee will be refund if it is found that vulnerabilities were either known about or in the process of being patched.

REFUND
Processing refunds always takes time. Cyber Espial will only refund the advance fee to a business bank account. The banking system specifies how long it typically takes for a transaction to reflect back.

WEBSITES REMAIN ORGANIZATIONS’ BIGGEST ATTACK VECTOR!
The majority of cybersecurity researchers concentrate their efforts on websites rather than IOT and cloud platforms, with businesses lacking a cyber vision being their top concern when reporting.
Want to speak with an expert how Vulnerability Reporting Program (VRP) can benefit your company with limited cybersecurity staff with timely and precise reporting to remediation?
Vulnerabilities prioritized with help of VRP assure that your team remediate the most critical threats with faster speed.
Learn more about program policy.
